Windows Server 2012 R2–use RD gateway to connect from Internet to internal PC remote desktop client.
Objective:

I want a simple solution to connect my own desktop via Remote Desktop Client when I am on the road.
Sometimes, port 3389 is blocked in client’s office. It is also risky to allow my PC for direct Internet connection. VPN is an option but it often require special software installation on the client side which sometimes is not allowed on customer’s PC. Another simple way is to use Windows Server 2012 RD Gateway as a proxy to my Desktop PC remote desktop.
I don’t need to use RemoteApp or VDI since only a small number of remote desktop is needed.
To make the case even more simpler, the RD gateway:
- No domain
- No RD Session Host, No Web Access. Only RD Gateway role is used.
Prerequisites:
- Config of firewall (1st firewall: open port 443 to RD Gateway; 2nd firewall: open from RD Gateway to PC (on need basis) port 3389 )
- Windows Server setup
- Enable Remote Desktop on Office PC.
Implementation Steps:
- Open Server Manager
- Open Server Manager – Add Roles and Features

- When asked for “Installation Type”, keep “Role-based or feature-based installation”

- For “Server Selection”, just select the server shown.
- For “Server Roles”, select “Remote Desktop Services”
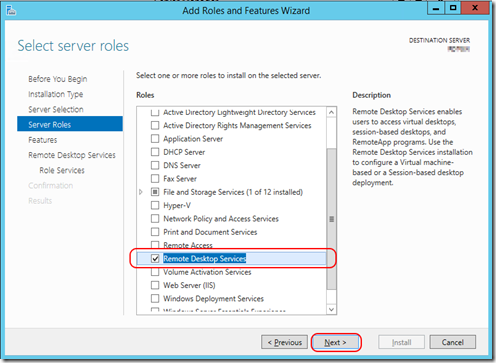
- For “Features”, no need to change.
- For “Role Features” under “Remote Desktop Services”, click
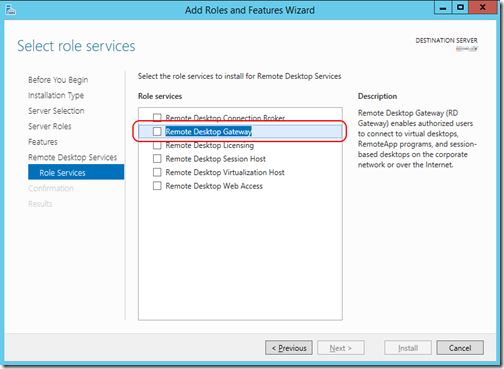
- You will be prompted to add additional features. Just press “Add Features” to accept what the system suggested.
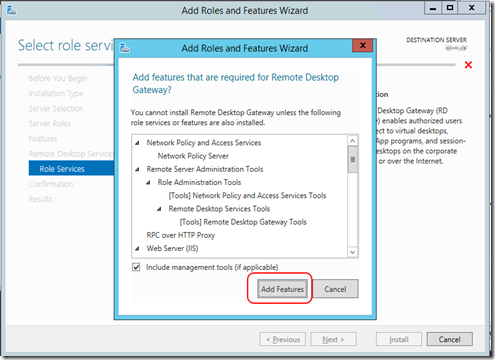
- Just click “Next” several times to accept all “Role Services” under Network Policy and Access (NPA) and IIS. When you reach the last page “Confirmation”, just click install.

- It may take several minutes for installation.
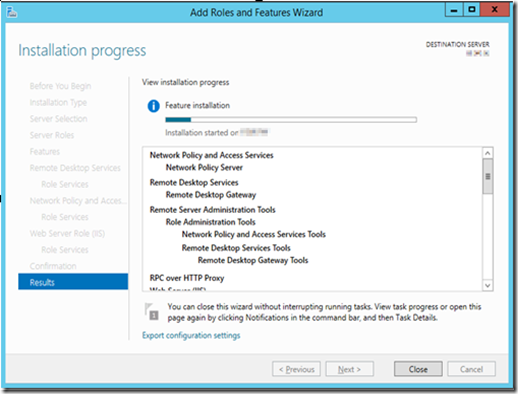
- After finish, I recommend to restart the server to ensure all files are installed.
Config Remote Desktop Manager:
- Open Server Manager. Enter “Remote Desktop Services”.

- No need to see “Overview”. Just click “Servers”. Right click on your server, then select “RD Gateway Manager”.

- You should see your server running.

- The dashboard will tell you what config is missed. We will start by setup the SSL certificate first. Click the link.
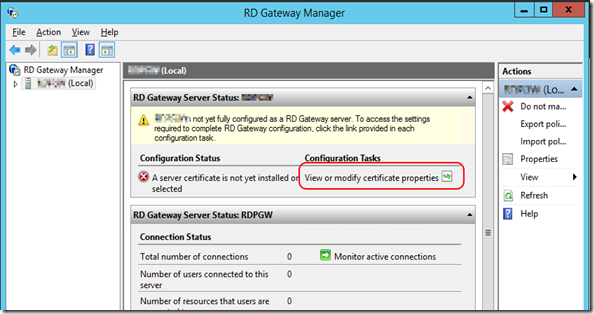
- The server properties page can also be opened by right-click the server and then select properties.
- The best case is to use a certificate from trusted CA (e.g. Verisign, StartCom, Trustico, etc). In this case, we will use a self-signed certificate.
- This certificate is not trusted by my notebook, thus the connection will not be accepted. In later step, we will talk about how to handle this.

- OR you can "Select an existing certificate" if you already have a working certificate, like that one for IIS.
- Enter your FQDN (e.g. rdgw.mydomain.net) in Certificate name. The system will also copy the certificate in side your Document folder. Press OK to generate the certificate. Copy the .CER file to your notebook as well.

- After the certificate is created/imported, you will see the info displayed.

- Next, go to Transport Settings. I will use all default setting.

- Next, go to RD CAP store. CAP means Connection Authorization Policies. It is about WHO can use this RD Gateway. I will use “Local server running NPS” (Network Policy Server).
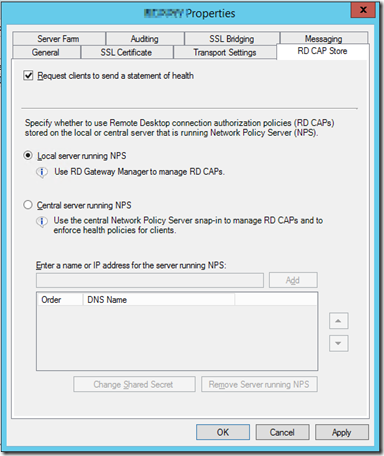
- Click OK to close the Properties page.
- After the basic server setting, we are going to config the CAP and RAP. Here’s the quick reference of the terms:
Connection Authorization Policies (CAP’s) - who can access resources behind the RDGW.
Resource Authorization Policies (RAP’s) - what resources (i.e. servers of farms) can be accessed by users authorized in CAP.
- Next, Let’s create Policy. Expand the tree under the server. Right-click on “Connection Authorization Policies” – “Create New Policy” – “Wizard”

- We will create CAP and RAP at the same time. Click Next to continue.

- Connection Authorization Policy – Enter a name for this policy (you can have multiple policy). Click Next.
- Requirements – Add a Windows user group as authorized user group for using RD Gateway. (I created one local computer group “RD GW users” for this purpose). Click Next.

- Device Redirection and Session Timeout – accept default setting in my case. Click Next.
- RD CAP Summary – nothing to set. Click Next.
- Resource Authorization Policy – enter RAP name. Click Next.
- User Groups – default will use the same user group used during CAP setup. Click Next.
- For Network Resource, it defines what servers this RD Gateway can be connected to. You can select the third one (allow any). If you want to be more secure, you can limit the allowed host by choosing the second option. (first option is not available because this server is not in domain.) Click Next.
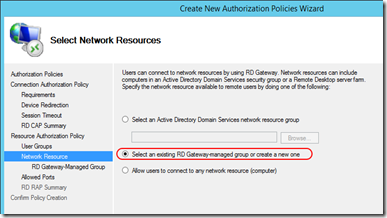
- In my case, I use the simplest form: IP address. I only allow the RD gateway to connect to one PC. Enter IP address and click “Add”. Click Next.

- Allowed Ports: use default value (Allow connections only to port 3389). Click Next.
- RD RAP Summary – just a summary. Click Next.
- CAP and RAP will be created. Click Close to close this wizard.
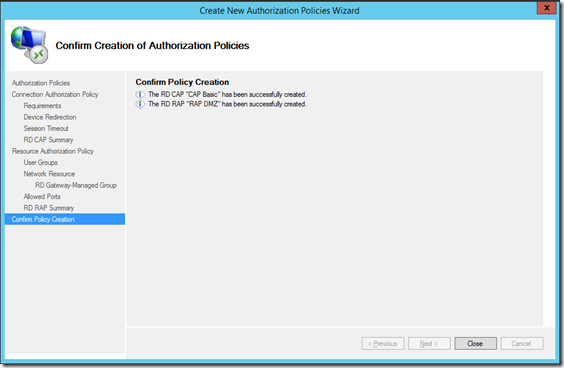
- Remember to set appropriate NAT at Firewall for port 443 (for RD Gateway) and 3389 (for Desktop PC remote desktop service).
To trust the server certificate in your notebook
This step can be skipped if your certificate is issued from a trusted CA. But I use a self signed certificate in this case.- Copy the CER file to your notebook. If you cannot find your certificate, you can browse to https://rdgw.yourdomain.net, and download the certificate via IE.

- Double click the CER file.
- Click “Install Certificate”.

- Select “Local Machine”. Click Next.
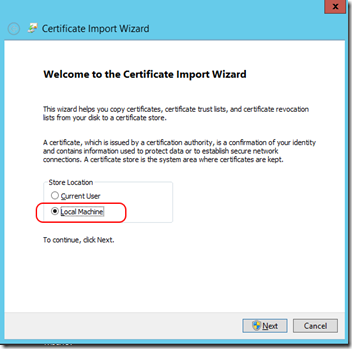
- Put the certificate into “Trusted Root Certificate Authorities”.
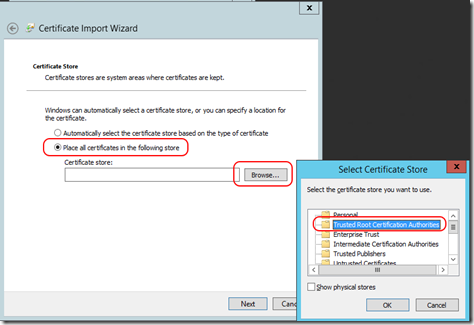
- Then Click Next and Finish.
- You will see a “Security Warning”. Click Yes to accept.


- Close and open IE again. Browse to the server. You will see there is no warning on the SSL certificate.

Connect to server using “Remote Desktop Connection”
- Open RDP client. Enter the computer (i.e. my Desktop PC internal IP).
- Click “Show Options”

- Click “Advanced” tab. Click "Settings”.
 .
. - Select “Use these RD Gateway server settings:”
Enter the FQDN name in “Server name”.
Uncheck “Bypass RD Gateway server for local addresses”.
I use separate ID for RD Gateway and my Desktop PC for double security. Uncheck “Use my RD Gateway credentials for the remote computer”
- Click OK connect.
- Enter the access credential for RD Gateway server. If you use domain account, enter your account name in DOMAIN\username format. As my RD gateway is in workgroup, I need to specify it is a local account by dot: .\username.
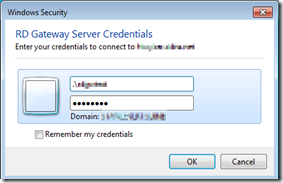
- Click OK to continue.
- Now, you will be prompted for another credential for my Desktop PC credential. You may click “Use another account” to enter another set of credential.
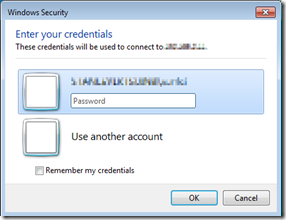
- Bingo! Now you can connect your office PC from Internet, with the simplest config, and two sets of password.
- On Windows 10 ver 1803, if you cannot connect to the server, try to add a new DWORD RDGClientTransport = 1 under HKCU\Software\Microsoft\Terminal Server Client\
Comments